Edge computing is one of the fastest growing areas in the industrial sector as organizations pursue Industry 4.0 opportunities to gain insight from assets at the edge. Over the next few years, IDC projects edge devices will generate more than 51% of global data. With increased information opportunities from Industry 4.0 data flow, cybersecurity risks also can increase.
While success at the edge offers significant potential, organizations identify cybersecurity as a critical issue to solve before fully pursuing opportunities at the edge. Operational technology (OT) and information technology (IT) teams must understand best practices and strategies to implement cybersecurity in these new environments and extend their security posture to edge locations.
Experts in the industry will have a robust discussion on how to “Fearlessly Implement Cybersecurity at the Edge,” in a Sept. 8 Control Engineering webcast. This panel discussion, designed to demystify emerging security concepts, will feature Barry Dellecese, Senior Director, Product Management and Product Marketing with Stratus Technologies; Dino Busalachi, CTO of Velta Technology; Jim Cook, COO of Velta Technology; and Robert Ruiz, Channel Sales Director at Claroty.
So what is edge computing and what can it do for an organization? The edge, in its simplest terms, is the physical location within a business where data is collected, analyzed and needed most. This varies based on the type of business.
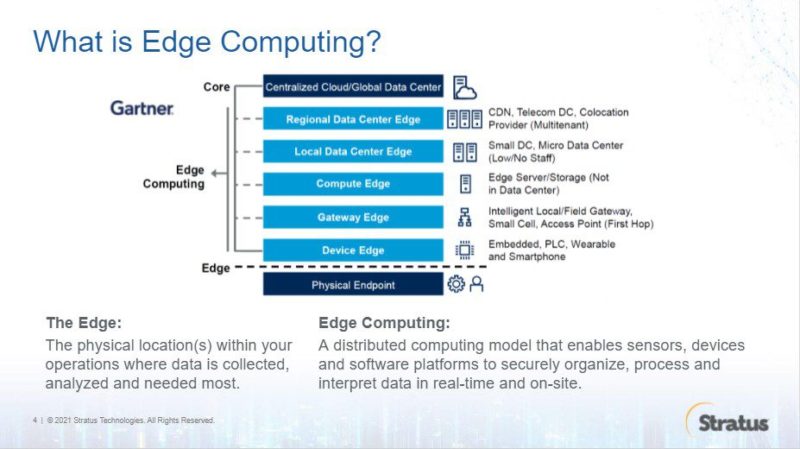
Edge computing is a distributed computing model in which computing takes place near or at the edge, often in collaboration with a centralized server or the cloud. This model enables the growing number of sensors, devices and software platforms being deployed at the edge to securely organize, process and interpret data in real time onsite.
Edge computing creates new and improved ways for leaders to:
- Maximize operational efficiency, improve performance and safety
- Ensure the availability of business-critical operations
- And automate processes.
Self-driving cars are a perfect example of edge computing. For safety reasons, it’s essential these vehicles can make quick adjustments as they deal with the complexities of the road. Delays or service outages can lead to catastrophe, so a self-driving car must receive data in real time for local processing in its own computer systems.
As companies rush to the edge, it’s also more likely threat actors will target edge applications in their attacks. Compromises at the edge can lead to serious issues that can extend beyond service disruptions and taking OT systems offline.
To better understand this risk, companies need to know how to gauge vulnerability and risk at the edge; strategies to drive process integrity for critical equipment and data in OT, Internet of Things (IoT) and Industrial Internet of Things (IIoT); approaches to securely deploy autonomous edge computing platforms; how to protect data transmission from edge to enterprise; and ways to communicate edge cybersecurity strategy across an organization through “compelling events.”
Moving to the edge can provide numerous benefits — speed being the primary one — but organizations need to understand what they’re getting into before they can truly make it work.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.








