
Common Sense and the CMMC: Expert Interview Series, Ryan Heidorn, Steel Root
Ryan Heidorn, co-founder and managing partner at Steel Root, walks DoD vendors through what they need to know about the CMMC

Ryan Heidorn, co-founder and managing partner at Steel Root, walks DoD vendors through what they need to know about the CMMC
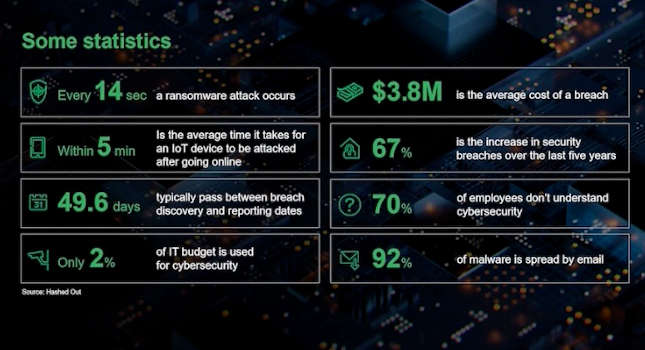
Manufacturing is undergoing some major changes and turning toward a digital transformation. Technology is becoming more intertwined with one another thanks to the Industrial Internet of Things (IIoT) and other concepts are bringing everything together. […]

Cybersecurity has become a major topic after recent high-profile attacks such as SolarWinds and the Oldsmar attack in Florida. Our work world continues to change due to COVID-19 and is forcing cybersecurity to the front […]

They fought the chip and the chip won. MORPHEUS, an “unhackable” computer chip developed by computer science researchers at the University of Michigan, lived up to its name in its first bug bounty competition. It […]

Video courtesy: CxEnergy Presenter: Derek Hedrick, Ameritech Data Solutions Why has Cybercrime become so prevalent? Because it’s easy, it’s hard to get caught, and it’s really profitable, generating more than $1.5 trillion in 2018 alone. Meanwhile, […]

If recent cyberattacks like SolarWinds and Oldsmar have demonstrated anything, it’s the vulnerability landscape in operational technology (OT) and manufacturing is changing rapidly – and not necessarily for the better. Risks are higher than ever […]

Seeq is co-sponsoring the Microsoft Energy Core Methane Emissions Hackathon virtual event. The objective of the hackathon is to overlay oil & gas asset and geographic information system data to pinpoint leak location, and to […]

Between the SolarWinds cyberattack and the smaller, but no less frightening, Oldsmar attack on a water treatment plant near Tampa Bay, Florida., cybersecurity has been front and center in the news. But these two cyberattacks […]

The Hackers’ Epoch: The Cybersecurity Card Game by Scruffy City Games helps students understand online threats and teaches them fundamental terms they’ll need to learn. After playing the game, when they read a news article […]

Featured articles in this eBook include stories on cybersecurity for IIoT robots, cybersecurity asset updates and using cybersecurity to improve tomorrow’s manufacturing operations.

Ryan Heidorn, co-founder and managing partner at Steel Root, walks DoD vendors through what they need to know about the CMMC

Manufacturing is undergoing some major changes and turning toward a digital transformation. Technology is becoming more intertwined with one another thanks to the Industrial Internet of Things (IIoT) and other concepts are bringing everything together. […]

Cybersecurity has become a major topic after recent high-profile attacks such as SolarWinds and the Oldsmar attack in Florida. Our work world continues to change due to COVID-19 and is forcing cybersecurity to the front […]

They fought the chip and the chip won. MORPHEUS, an “unhackable” computer chip developed by computer science researchers at the University of Michigan, lived up to its name in its first bug bounty competition. It […]

Video courtesy: CxEnergy Presenter: Derek Hedrick, Ameritech Data Solutions Why has Cybercrime become so prevalent? Because it’s easy, it’s hard to get caught, and it’s really profitable, generating more than $1.5 trillion in 2018 alone. Meanwhile, […]

If recent cyberattacks like SolarWinds and Oldsmar have demonstrated anything, it’s the vulnerability landscape in operational technology (OT) and manufacturing is changing rapidly – and not necessarily for the better. Risks are higher than ever […]

Seeq is co-sponsoring the Microsoft Energy Core Methane Emissions Hackathon virtual event. The objective of the hackathon is to overlay oil & gas asset and geographic information system data to pinpoint leak location, and to […]

Between the SolarWinds cyberattack and the smaller, but no less frightening, Oldsmar attack on a water treatment plant near Tampa Bay, Florida., cybersecurity has been front and center in the news. But these two cyberattacks […]

The Hackers’ Epoch: The Cybersecurity Card Game by Scruffy City Games helps students understand online threats and teaches them fundamental terms they’ll need to learn. After playing the game, when they read a news article […]

Featured articles in this eBook include stories on cybersecurity for IIoT robots, cybersecurity asset updates and using cybersecurity to improve tomorrow’s manufacturing operations.
Keep your finger on the pulse of top industry news
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.