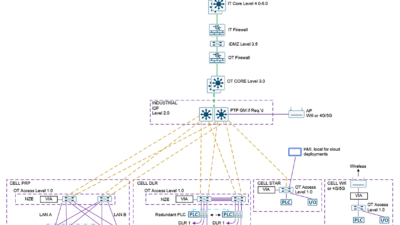
Integrated control and safety systems can simplify a strong cybersecurity posture for a manufacturer.

Learning Objectives
- Control system integration is crucial for critical systems in the plant: the basic process control system (BPCS) and safety instrumented system (SIS).
- Control system integration is only as good as the security system behind it.
- An integrated system provides the logical separation plants need while improving security at a smaller footprint.
As more organizations embrace digital transformation, they have come to see how integration is critical for security, efficiency and scaling. That same line of thinking applies to the most critical systems in the plant—the basic process control system (BPCS) and safety instrumented system (SIS).
Many organizations think it’s more secure to “separate” control and safety systems with an interfaced architecture to avoid “putting all their eggs in one basket.” However, having more “baskets” means increasing the potential exposure to risk. The key is not the number of baskets, but how well each basket is protected.
It is easier and more secure to integrate the safety and control systems, and then properly defend the overall architecture. Integration does not eliminate the separation between the distributed control system (DCS) and SIS. The SIS and DCS are still separate, but security is simplified.
Separate DCS, SIS does not necessarily mean secure
The most common reason organizations choose separated systems for control and safety is the perceived increase in security. On the surface, this idea appears to have merit. Because the systems are separated, it seems harder for a bad actor to leverage vulnerabilities in the BPCS and cause problems in the SIS. However, separation does not mean isolation. An SIS is typically connected to the DCS, providing an attacker three possible targets:
- The SIS
- The DCS
- The interface between SIS and DCS, as well as any other interface to the SIS.
The SIS needs additional protections beyond the perceived separation in an interfaced system. The most critical element of a good security posture is defense-in-depth, which creates layers of protection around a system to help defend against outside and internal interference. Each potential entry point to the SIS must be secured via multiple layers of protection.
DCS, SIS vulnerability to fix
One key example of why entry points must be defended is operations, such as maintenance bypasses, on the SIS are normally set from the DCS. Unless there are mechanisms in place to prevent unauthorized actions, an attacker who compromises the DCS may be able to set bypasses that defeat the safety function. The SIS might consider these operations as valid and proceed. An interfaced system does not necessarily provide more protection against this threat.
A system is only as secure as its weakest link. Any interface to the SIS could be the weakest element unless properly protected (using, for example, a defense-in-depth approach). “Separate” systems are often connected via an open protocol such as Modbus or OPC. Security on these open protocols is dependent on proper configuration of the security of those protocols on both systems, increasing the potential for errors that create access loopholes.
Separating an SIS and DCS can increase the complexity of the interface without delivering any additional benefits to cybersecurity. In fact, separation can create cumbersome interfaces that increase cybersecurity risk footprint and limit the flexibility and scalability that are essential to get the most benefit from digital transformation in the plant.
An interfaced system can be properly protected; however, having separated systems means maintaining independent defense-in-depth architectures for each system, and possibly additional measures for the engineered connection between the systems. Some of the defense layers (e.g. antivirus) are going to be identical on each system, so having two separate systems doesn’t offer more protection than having only one; it just means more work to install and maintain.
Proper SIS/DCS integration increases security
Integration does not mean less separation. Safety-critical components are still separated from the rest of the system. The interface to the DCS components is via a built-in interface based on proprietary protocols. With a well-designed integrated system, the number of entry points to safety-critical components is lower than on most interfaced systems.
There are often more interfaces to the SIS than users realize. In addition to the DCS interface, the SIS might have connectivity to asset management systems (AMS), process information management systems (PIMS) and safety lifecycle management systems (SLMS). While it is possible to secure all these interfaces, there is significant effort associated. On an integrated system, there is only one interface to the SIS; all other systems communicate through the BPCS.
One SIS interface means organizations employing an integrated architecture manage a unified defense-in-depth system to protect the control and safety systems. This simplified architecture leads to shorter install times and easier management.
Proper integration helps bridge the IT/OT gap
A control and safety system architecture must not only meet the approval of the operations team, but also must fit the architecture and standards the information technology (IT) and operations technology (OT) departments have in place. Bridging this gap is a critical driver for digital transformation. A complex architecture of engineered links between two separate systems is more difficult to secure, which creates more burdens for IT and OT management. This leads to longer implementation and approval times for the original project and any future changes.
An integrated control and safety system removes many of the obstacles that make both systems difficult for IT and OT to implement and manage. Intuitive configuration and management tools make integrated systems easier to adjust to IT and OT policies and practices and simplify change management as the system ages and expands. Most integrated systems provide secure proxy access out-of-the-box for monitoring and management tools.
BPCS and SIS: Separate versus integrated systems
An organization’s safety system and control system must be properly secured, but the architecture used is only one part of overall security. Opting for separated architecture is no more secure than choosing a properly designed integrated system. The primary difference between the two systems is the ease of connecting, configuring and securing the BPCS and SIS. An integrated system provides the logical separation plants need, while providing a smaller security footprint to maintain and more flexible and intuitive options for defense-in-depth.
Sergio Diaz is DeltaV SIS product manager, Emerson. Edited by Chris Vavra, associate editor, Control Engineering, CFE Media and Technology, [email protected].
MORE ANSWERS
Keywords: safety instrumented system, distributed control system, SIS, DCS
Consider this
What is the biggest challenge your company has faced when integrating control systems?