The convergence of information technology (IT) and operations technology (OT) can make manufacturing operations more streamlined and efficient. Getting there, though, is a challenge in of itself. This has become one of the major challenges for manufacturers, and while it isn’t as fraught as it used to be, challenges remain.
Eric Knopp, business manager for Rockwell Automation, said, “The cybersecurity threat is real in manufacturing. And it’s costly not just from a production standpoint, but from a public relations standpoint,” in the presentation “The Next Phase of the IT/OT Integration: Extending IT Security to the Cell/Area Zone of the Plant Architecture,” at Automation Fair at McCormick Place in Chicago.

Security challenges for industrial networks
Knopp said companies need to have an effective cybersecurity plan in place. The problem is what qualifies as a priority for the IT team might not resonate in the same way on the plant floor.
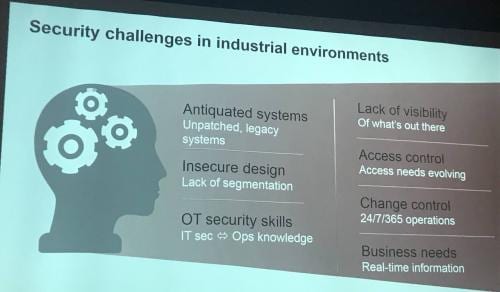
There are many security challenges in industrial environments, but two of the most notable, Knopp said, are a lack of visibility and insecure design.
“In the IT space,” Knopp said, “everything is structured. In the OT space, it’s very common that the networks are thrown together as you go. As a result, the first step many customers have to take is determine what is and isn’t on the network. You can’t move forward if you don’t have an idea of what assets you have.”
With insecure design, it’s about a lack of segmentation. Knopp said that while customers have gotten good with the IT/OT separation with the firewall, there are still problems horizontally on the OT level. “Do you have your machines segmented in such a way so a bad actor doesn’t have access to the whole breadth of the network when they access one controlled or machine?” Knopp said.
Software-defined security strategy
Knopp said software-defined technology is not as familiar to OT as it is to IT, but that is changing. Software-defined technology has been prevalent in IT and it can drive efficiency on the manufacturing floor.
Co-presenter Paul Didier at Cisco added context, saying, “Software-defined is a big concept on the IT and enterprise side and its driving efficiencies. A lot of this stuff is available in open application programming interfaces (APIs). It helps automate configuration and operation of the network. For OT, that’s very attractive because it simplifies and avoids the scaling and training issues.”
There is a caveat, however, to software-defined technology when it comes to OT. “We are not ready to deploy in a manufacturing environment. It’s not mature enough. There’s a lot of work to be done on both sides to bring these things together. Keep it focused on the enterprise. Security is where software-defined concepts will start and that’s appropriate.”
As IT/OT convergence continues, it’s crucial to have an industrial security framework. The framework, Didier said, should have a defense-in-depth approach consisting of five phases:
- Access, segmentation, and policy
- Threat detection
- Behavior analysis
- Content protection
- Cloud security and threat intel.
To keep the IT and OT worlds separate and secure, an industrial demilitarized zone (IDMZ) can help. If information or access is needed on one side to the other, the IDMZ acts as a place where both sides can meet and exchange information as needed within a secure context.
Even with that, Didier said, there are challenges. “We see very frequently as these two worlds are colliding there is some friction. Part of that is because there’s things the IT folks understand related to security the OT folks don’t understand. OT understands context related to the devices, etc., and what is needed regarding assets.”
It’s all about context in the end. Give the OT user the context they need in a manner they can understand and provide them with the tools to do their job safely and securely.
Three ways to merge IT and OT insights
IT and OT can help each other, Didier said, in several ways to make the flow of information a little smoother. He cited three use case examples on how they can do that.
1. Monitoring flows and anomaly detection. Didier said this is the first step in the process. IT monitors traffic lows and detect anomalous traffic behavior so the source can be identified. “You need to do this before you implement anything,” Didier said. “This is about discovering the network, and who’s talking to who for context.”
2. Cell/area zone segmentation. This requires visibility of industrial automation and control systems (IACS) in the production environment. From there, companies can segment the industrial network so IACS devices can communicate with each other in the cell/area zone. IT and OT, Didier said, create a policy chart that everyone is onboard with. “It’s relatively easy to manage, but they require previous knowledge of who’s talking to who. Once they’ve been written, it’s easy to implement in a relatively simple matrix,” he said.
3. On-demand remote access. This allows OT to manage access as defined by IT security. A specific asset in the machine being serviced must be accessible to the machine building over a remote virtual private network (VPN). There’s no dependency on IT to enable access during the maintenance window, which reduces downtime.
While a full convergence might not be happening anytime soon, there are many steps manufacturers can take to make the process easier.
Chris Vavra, web content manager, Control Engineering, CFE Media and Technology, [email protected].
ONLINE extra
Read additional stories from the author from prior trade events.
RELATED ARTICLES
Industrial control system (ICS) cybersecurity advice, best practices
https://www.industrialcybersecuritypulse.com/industrial-control-system-ics-cybersecurity-advice-best-practices/
Manufacturers need to prepare for cybersecurity threats
https://www.industrialcybersecuritypulse.com/manufacturers-need-to-prepare-for-cybersecurity-threats/
ICS cybersecurity company appoints CEO
https://www.industrialcybersecuritypulse.com/ics-cybersecurity-company-appoints-ceo/
Original content can be found at Control Engineering.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.