The U.S. Department of Defense (DoD) supply chain has been under attack. This year’s ransomware events — such as the ones faced by a U.S. maritime base that brought cameras, door-access control systems and critical monitoring systems down for 30 hours, as well as those on defense suppliers such as CPI, EWA, Westech International, Garmin, ST Engineering, Visser and Kimchuk — should serve as a warning. Organizations of all types and sizes in the defense industrial base (DIB) have faced cyberattacks. In fact, enterprises like DMI that provide managed information technology (IT) and cybersecurity services to organizations like NASA and Fortune 100 companies have also been breached.
Cybersecurity vulnerabilities and intrusions pose major risks to the DoD and its supply chain in the form of business disruptions, national security issues, and diminishing trust in the government and companies. According to IBM, cyberattacks against industrial targets doubled in 2019. These events reinforce the DoD’s decision to require compliance to Cybersecurity Maturity Model Certification (CMMC).
While cybersecurity requirements have been a part of the defense procurement process for some time now in the form of the NIST 800-171 compliance, CMMC compliance standardizes the adherence to cybersecurity requirements with more comprehensive practices and higher degrees of maturity, as highlighted in the following sections.
Certification:
The NIST 800-171 requirement mandated self-assessment and self-attestation of compliance. On the other hand, CMMC requires a third-party auditor to certify that an organization has met the requirements outlined for the business. The certification will be valid for three years. The CMMC Accreditation Body (CMMC-AB), a nonprofit organization, has been chartered to develop training, audit and certification standards for the auditors. The entity is in the process of releasing the provisional class of accredited auditors (C3PAO).
An organization will have to comply to one of the CMMC’s five levels depending on its exposure to federal contract information (FCI) and/or controlled unclassified information (CUI). The higher the level, the more cybersecurity practices and higher degree of maturity of those practices are required.
Comprehensiveness:
CMMC compliance requires institutionalization of up to 171 practices, about 55% more than NIST SP 800-171, across 17 different business areas with an appropriate level of cross-functional engagement and governance. CMMC incorporates practices from NIST SP 800-171, the UK’s cyber essentials, Australia’s Cybersecurity Centre essential eight maturity model, the Aerospace Industries Association’s NAS9933 and others.
Maturity:
The maturity requirement is often not well understood by organizations. It isn’t sufficient to institutionalize a practice; the organization has to demonstrate an appropriate level of excellence at the practice. For example, level one requires an ad-hoc use of the practice, whereas level three requires an appropriate level of resources and plans in place for the practice. An organization requiring level four of compliance will need quantitative measures for the practices in place and frequent reviews of performance by the management team. This requires continuous gap assessment, timely remediation and governance in a programmatic approach.
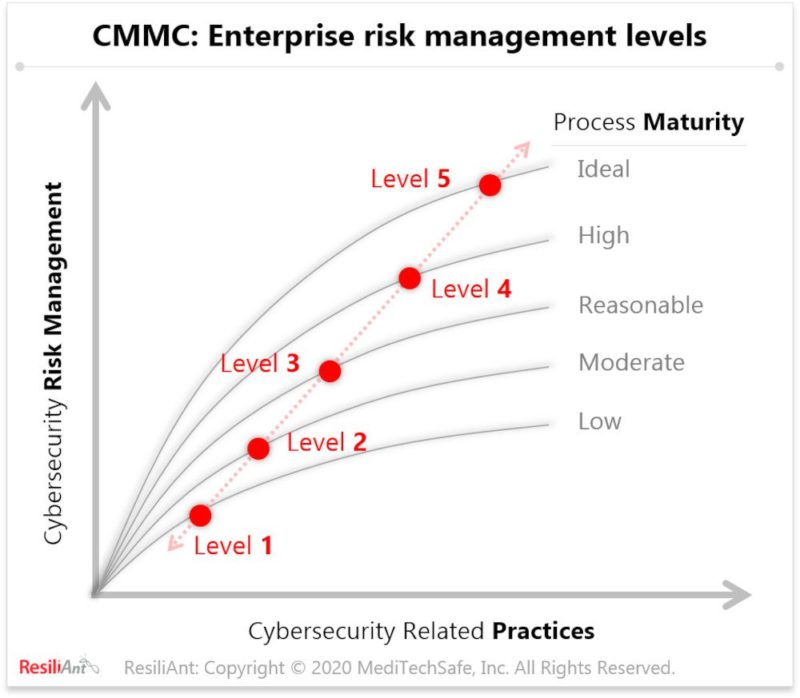
Who needs to comply and at what level?
All organizations in the DoD direct and extended supply chain (DFARS flow-down) that are exposed to FCI and/or CUI will have to comply to CMMC. An organization that is exposed to only FCI will need to comply at level one requirements. On the other hand, an organization that is exposed to DoD sensitive CUI will have to protect CUI and reduce the risk of advanced persistent threats.
- Level 1: Basic Safeguarding of FCI
- Level 2: Transition Step to Protect CUI
- Level 3: Protecting CUI
- Level 4-5: Protecting CUI and reducing risk of Advanced Persistent Threats
All organizations can benefit from having a higher degree of process maturity in cybersecurity practices from an enterprise risk management perspective.
Expected timeline:
The CMMC requirements are expected to be in request for proposal (RFP) from the fall of 2020, and actual clauses are expected to be in the contracts starting in winter/spring 2021.
Recommendations:
All organizations seeking certification by winter/spring of 2021 should start the gap assessment process against CMMC requirements now, remediate the gaps and demonstrate process maturity to gain certification. Starting early would allow an organization to gain certification in a timely manner. It’s highly recommended organizations take a programmatic approach and be intimately involved in the compliance process because of the breadth and depth of the requirements. CMMC compliance will not only help an organization win new defense business, but also help in enhancing overall security and risk management in the organization.
– This article originally appeared in Resiliant’s Knowledge Center. Resiliant is a CFE Media content partner.
Original content can be found at www.resiliant.co.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.








